
Malware
Malware is a malicious software that is created by cybercriminals to steal data and harm devises. Some types of malware are viruses, worms, Trojans, spyware, adware, and ransomware.
Select to learn more
Phishing
Phishing is when somoene tricks you into giving away any sensitive data by pretending to be some trusted source in emails or websites.
Select to learn more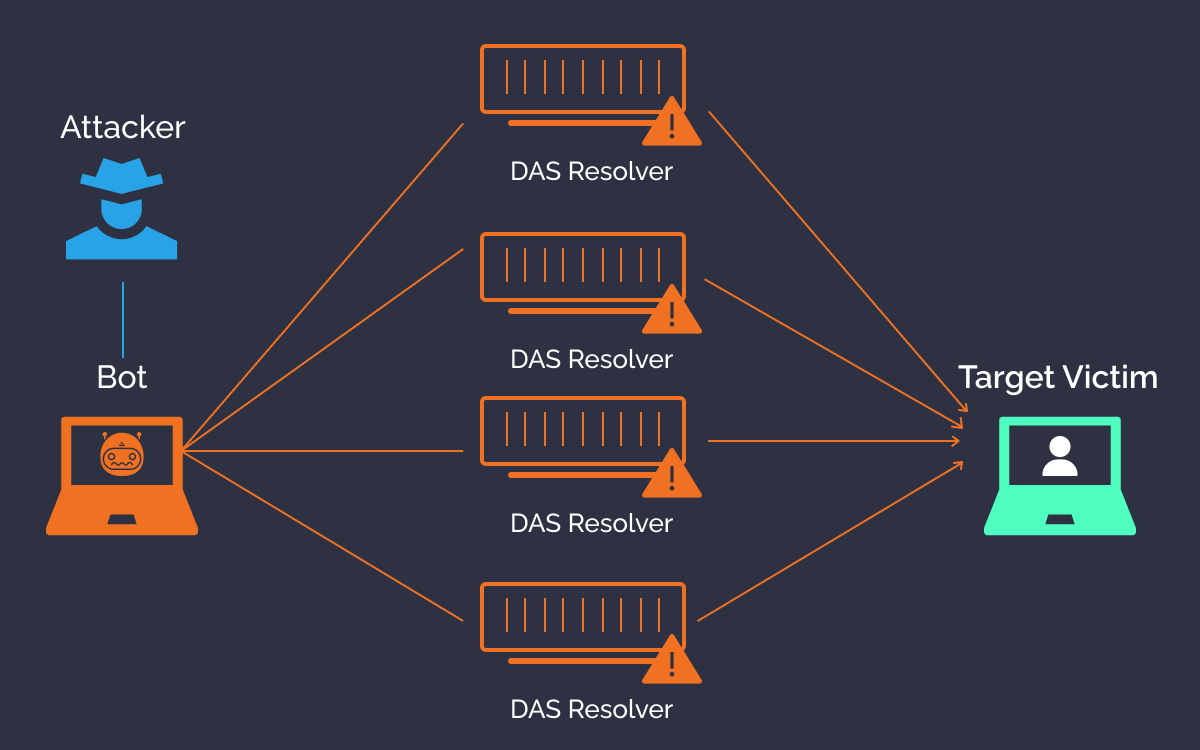
DDoS Attacks
DDoS attack aim to take down website or online sevice by overwhelming it with too many request, causing it to crash and become not accessible.
Select to learn more
Insider Threats
Insider Threats are risk from withing an organization that happens when someone with access, like an employee or contractor, misuses it to harm the organiztion network, system, or data.
Select to learn more
Social Engineering
SSocial Engineering is a tatic of maniputlating , unfluencing , or decieving a victim in order to steal personal information.
Select to learn more
Zero-Day Exploits
Zero-Day Exploits is an attack were cybercriminal use hidden flaws in software or hardware.
Select to learn more
Man-in-the-Middle
Man-in-the-Middle is when someone gets between you and a system to spy on or change the data passing through.
Select to learn more
Credential Theft
Credential theft is when someone steals your identity proof, giving them the access that you have also.
Select to learn more
SQL Injection
SQL injection is tatic were an attacker uses SQL code to hack into a database and get valuable information.
Select to learn more
IoT Vulnerabilities
IoT Vulnerabilities can create new ways for hackers to get into other devices on your home network.
Select to learn more